In the previous post, i showed how we synchronize secret from Vault to k8s, today with external-secrets.io i will guide you how to sync secret from AWS Secret Manager to k8s.
I will use minikube for demo purpose, also installing external-secrets using helm . Before working with CLI, i will create a alias kubectl and helm.
alias k=kubectl
alias h=helmIn the context of this post, i will
- install
external secretusinghelm - create a secret on
aws, name itk8s-dev/api - create a
aws iam access keyforexternal secret - sync
k8s-dev/apitodevnamespace onk8s
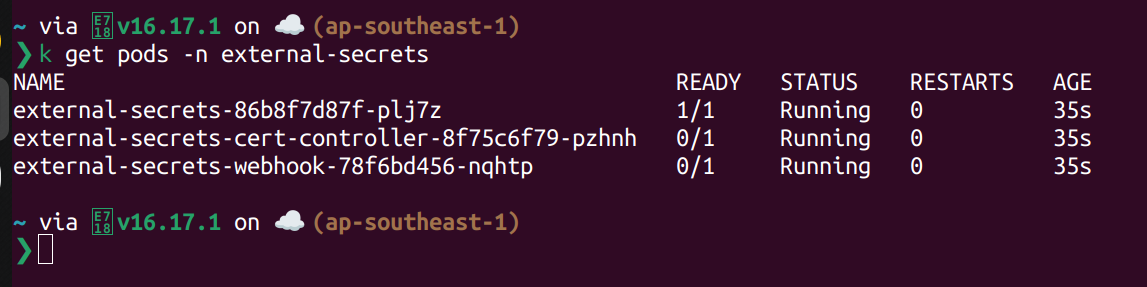
Install External Secret Operator on K8s.
Install using helm
h repo add external-secrets https://charts.external-secrets.io
h install external-secrets \
external-secrets/external-secrets \
-n external-secrets \
--create-namespace \
--set installCRDs=true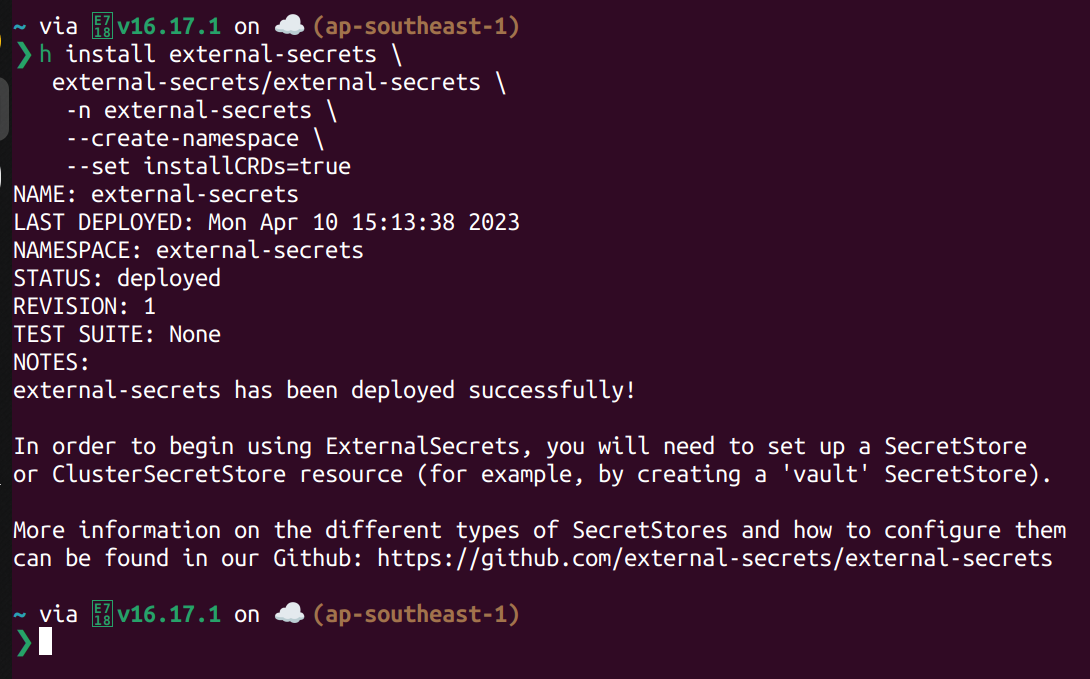
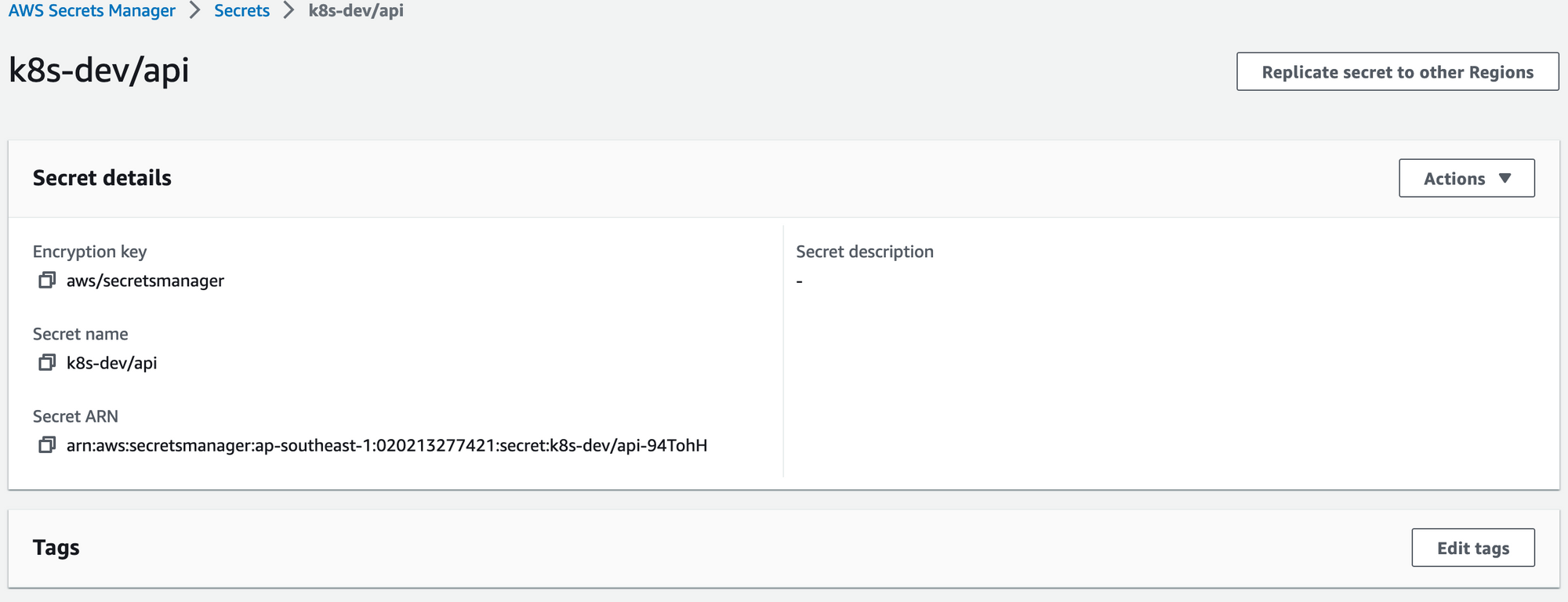
Create Secret On AWS Secret Manager.
I will create a key-vault secret using aws console. Name it k8s-dev/api, the secret's content is
{
"PORT": 5000,
"USERNAME": "hello"
}
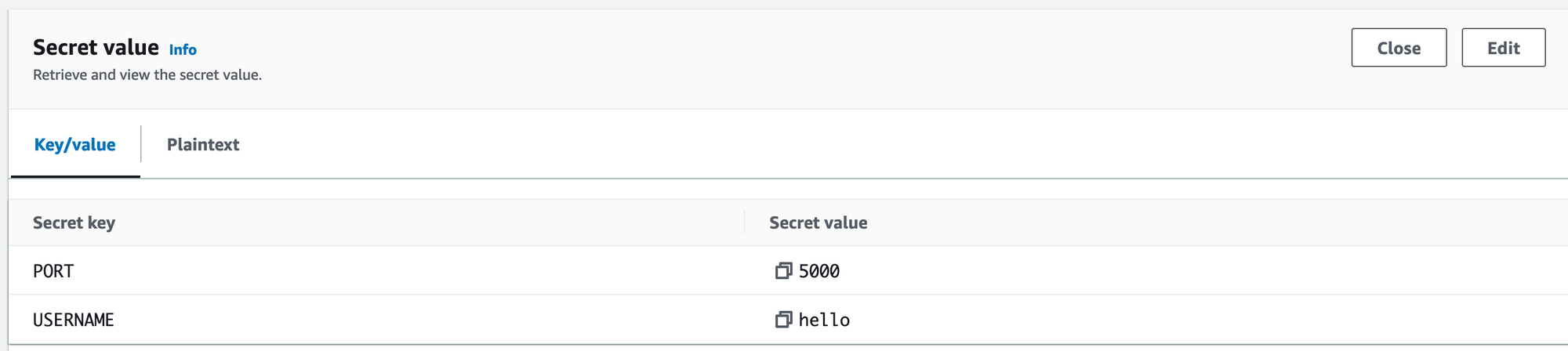
Create AWS Iam Key.
For demo purpose, i will create a iam user key that have permission to retrieve every secret started with k8s-dev secret.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "readprefixk8sdev",
"Action": [
"secretsmanager:GetResourcePolicy",
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret",
"secretsmanager:ListSecretVersionIds"
],
"Effect": "Allow",
"Resource": "arn:aws:secretsmanager:ap-southeast-1:020213277421:secret:k8s-dev/*"
}
]
}For me after creating key i got this key pair. (This key will be deleted after done this post, so don't waste your time to copy it).
{
"aws_access_key_id" = "AKIAQJNGOELWWV2OXODN"
"aws_secret_access_key" = "iOPJoGK7R2aaqG64fy4WXw8kXGTZ2GmtcWcFdgOc"
}Create Secret Store on K8S.
I will create a SecretStore crd in dev namespace. Remember to change your key pair.
First create dev namespace.
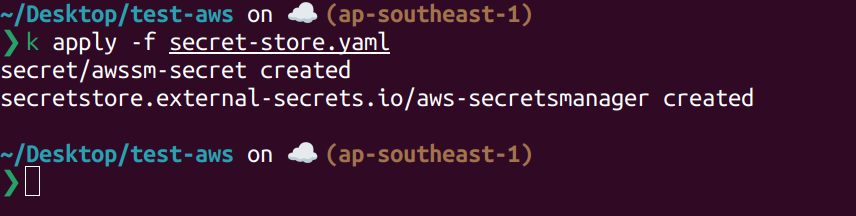
Create Secret Store crds, i also create a secret to save key pair value.
apiVersion: v1
kind: Secret
metadata:
name: awssm-secret
namespace: dev
type: Opaque
stringData:
access-key-id: AKIAQJNGOELWWV2OXODN
secret-access-key: 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
---
apiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: aws-secretsmanager
namespace: dev
spec:
provider:
aws:
service: SecretsManager
region: ap-southeast-1
auth:
secretRef:
accessKeyIDSecretRef:
name: awssm-secret
key: access-key-id
secretAccessKeySecretRef:
name: awssm-secret
key: secret-access-key
Using kubectl to create it.
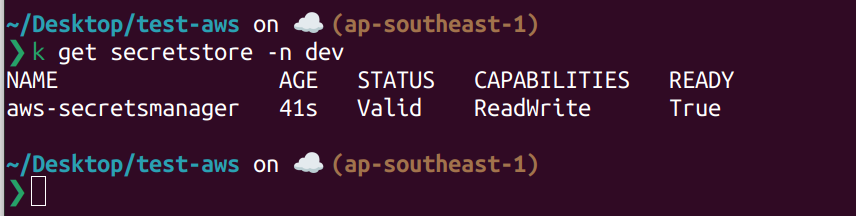
Using kubectl to retrieve this custom resource definition.
Sync Secret to K8S.
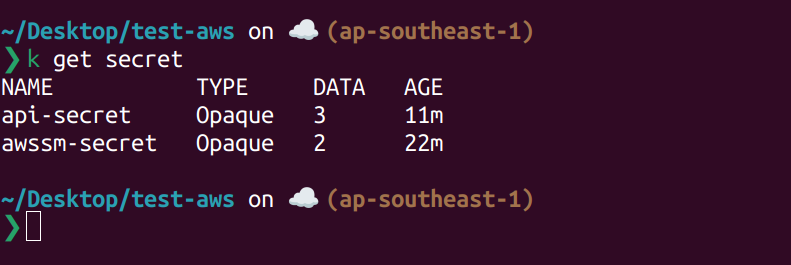
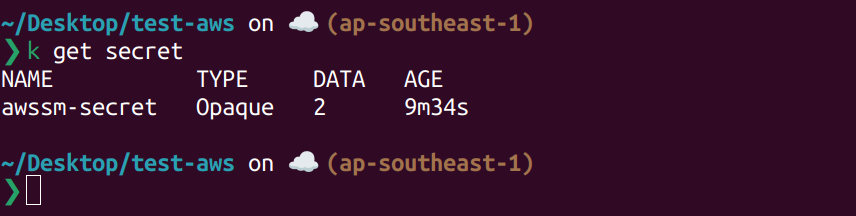
Currently on dev namespace, we only have awssm-secret.
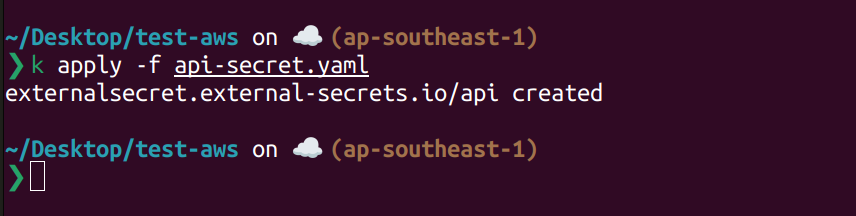
Let create another ExternalSecret crd to synchronize k8s-dev/api secret to k8s. The content of api-secret.yaml is like this.
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: api-secret
namespace: dev
spec:
refreshInterval: 5s
secretStoreRef:
name: aws-secretsmanager
kind: SecretStore
target:
name: api-secret
creationPolicy: Owner
dataFrom:
- extract:
key: k8s-dev/apiCreating using kubectl
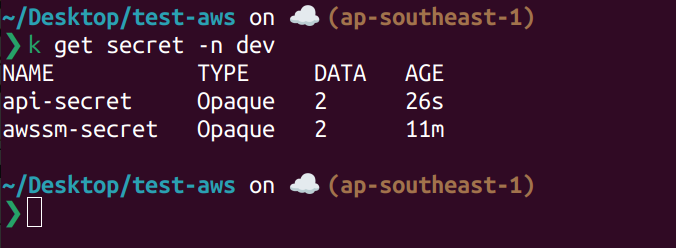
List current secret on dev namespace.
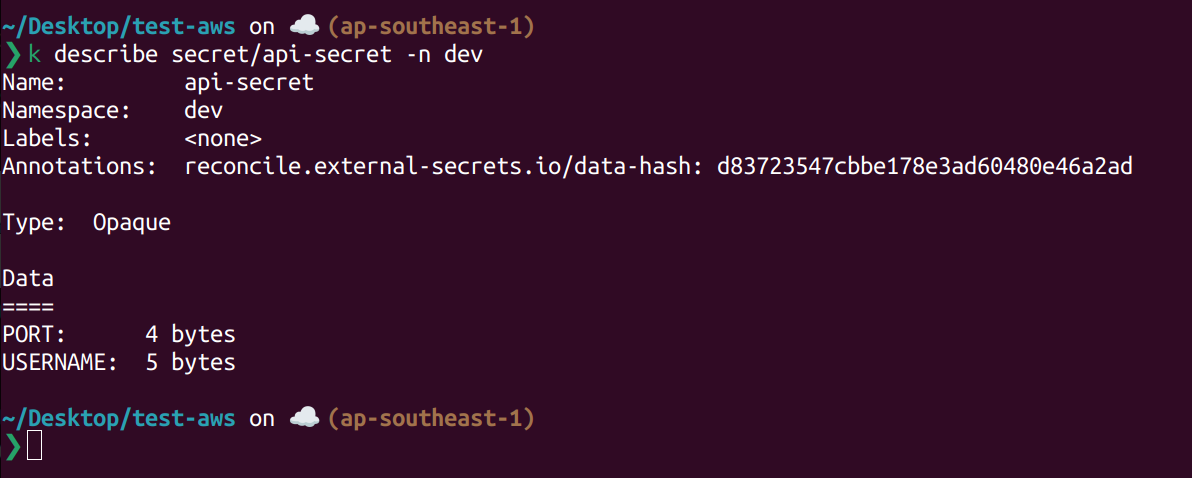
Describe api-secret secret.
Edit secret using AWS Console.
Open aws console update this secret, i will add another field called PASSWORD to this secret.
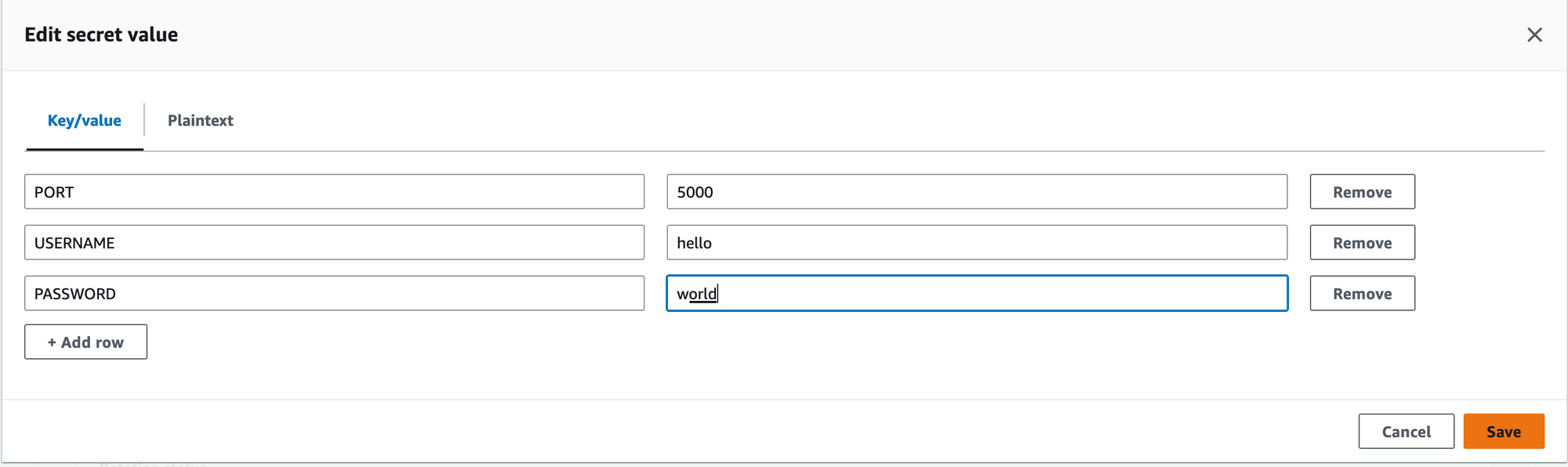
Save it and wait for 5s, it will be synced to k8s. Describe it again you will see the content was updated
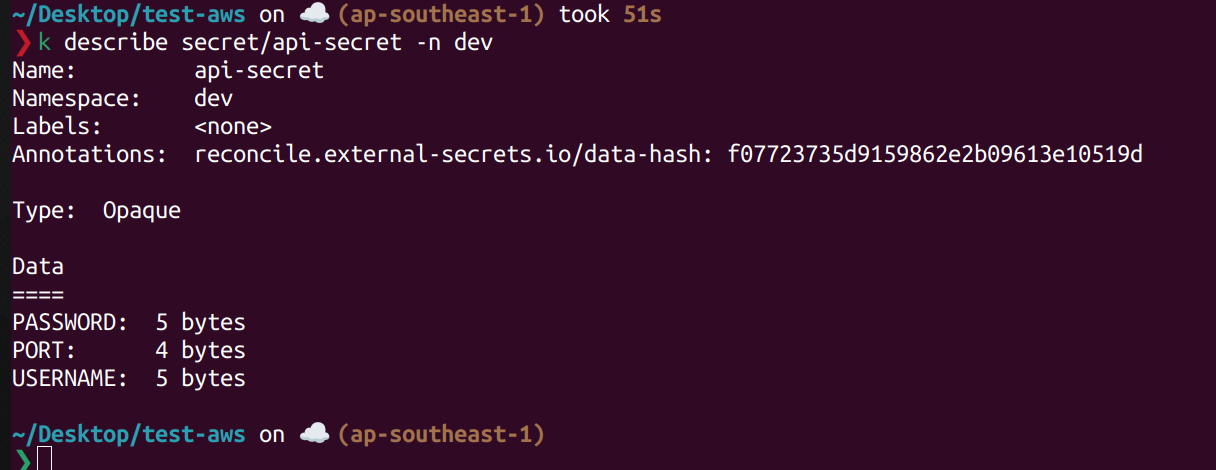
If you want to sync more secret, simply create more ExternalSecret crd. Thank for reading this post.