What is SSO?
SSO (single sign-on) in the enterprise refers to the ability for employees to log in just one time with one set of credentials to get access to all corporate apps, websites and data for which they have permission. SSO solves key problems for the business by providing:
- Greater security
- Improved usability and employee satisfaction
- Lower IT costs
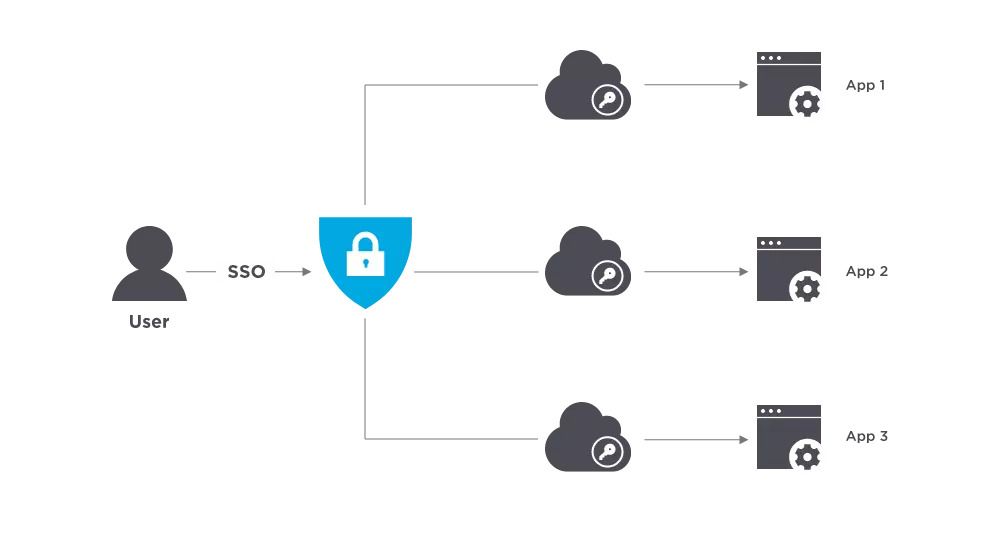
Benefits of SSO
Usernames and passwords are the main target of cybercriminals. Every time a user logs into a new application, it’s an opportunity for hackers. SSO reduced the number of attack surfaces because users only log in once each day and only use one set of credentials.
What is Amazon Cognito?
Amazon Cognito lets you easily add user sign-up and authentication to your mobile and web apps. Amazon Cognito also enables you to authenticate users through an external identity provider and provides temporary security credentials to access your app’s backend resources in AWS or any service behind Amazon API Gateway. Amazon Cognito works with external identity providers that support SAML or OpenID Connect, social identity providers (such as Facebook, Twitter, Amazon) and you can also integrate your own identity provider via SAML protocol.
The two main components of Amazon Cognito are user pools and identity pools. User pools are user directories that provide sign-up and sign-in options for your web and mobile app users. Identity pools provide AWS credentials to grant your users access to other AWS services.
A user pool is a user directory in Amazon Cognito. Your app users can sign in either directly through a user pool, or federate through a third-party identity provider (IdP). The user pool manages the overhead of handling the tokens that are returned from social sign-in through Facebook, Google, Amazon, and Apple, and from OpenID Connect (OIDC) and SAML IdPs. Whether your users sign in directly or through a third party, all members of the user pool have a directory profile that you can access through an SDK.
With an identity pool, your users can obtain temporary AWS credentials to access AWS services, such as Amazon S3 and DynamoDB. Identity pools support anonymous guest users, as well as federation through third-party IdPs.
How to configure Amazon Cognito User Pool ?
Click on Manage User Pools button and go through the user-friendly setup flow.

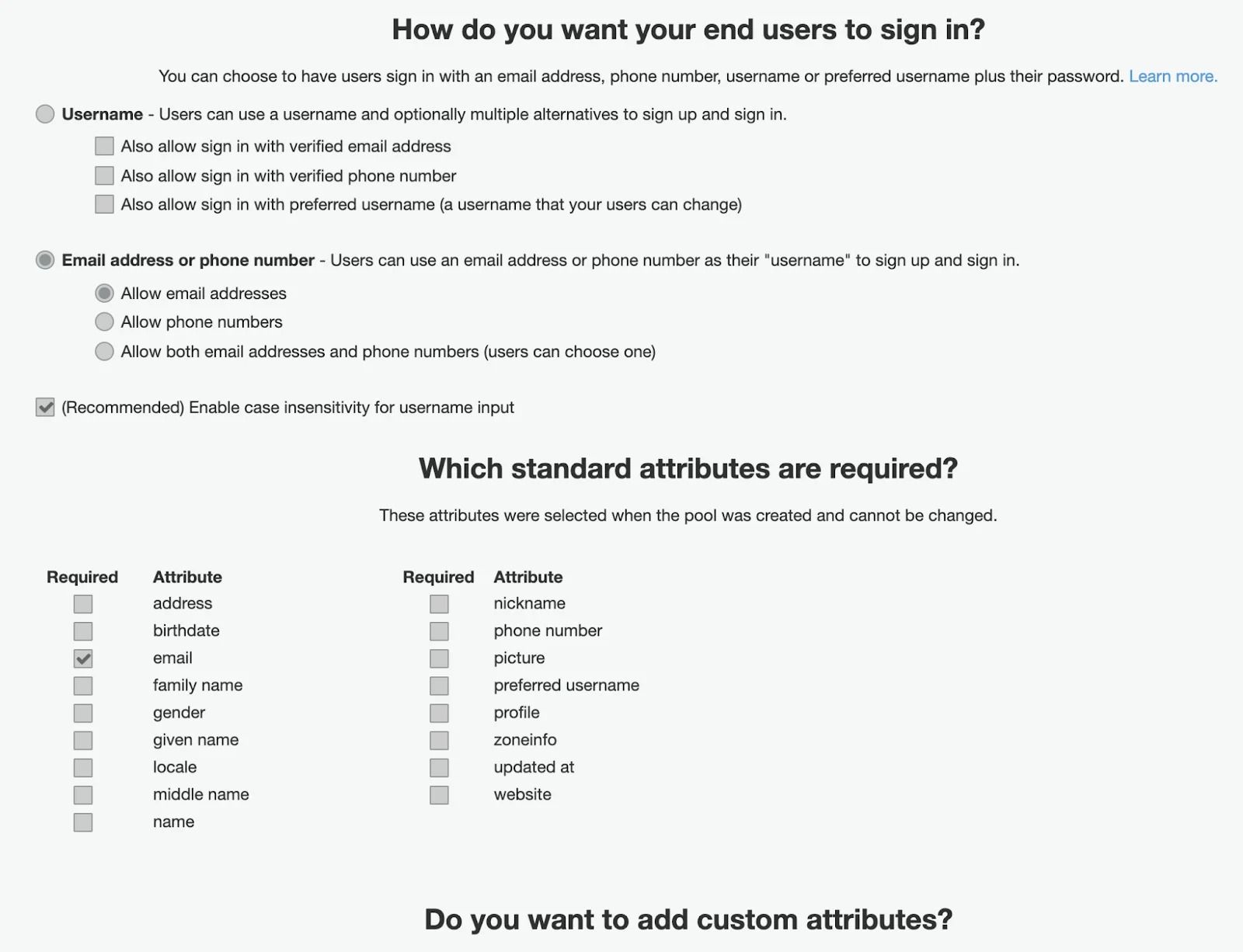
There you can configure Multi-Factor Authentication (it’s not needed if it’s a part of a flow for your SSO you are integrating with). Settings to recover a password — only if you allow your users to directly sign up through Cognito having their own set of credentials.

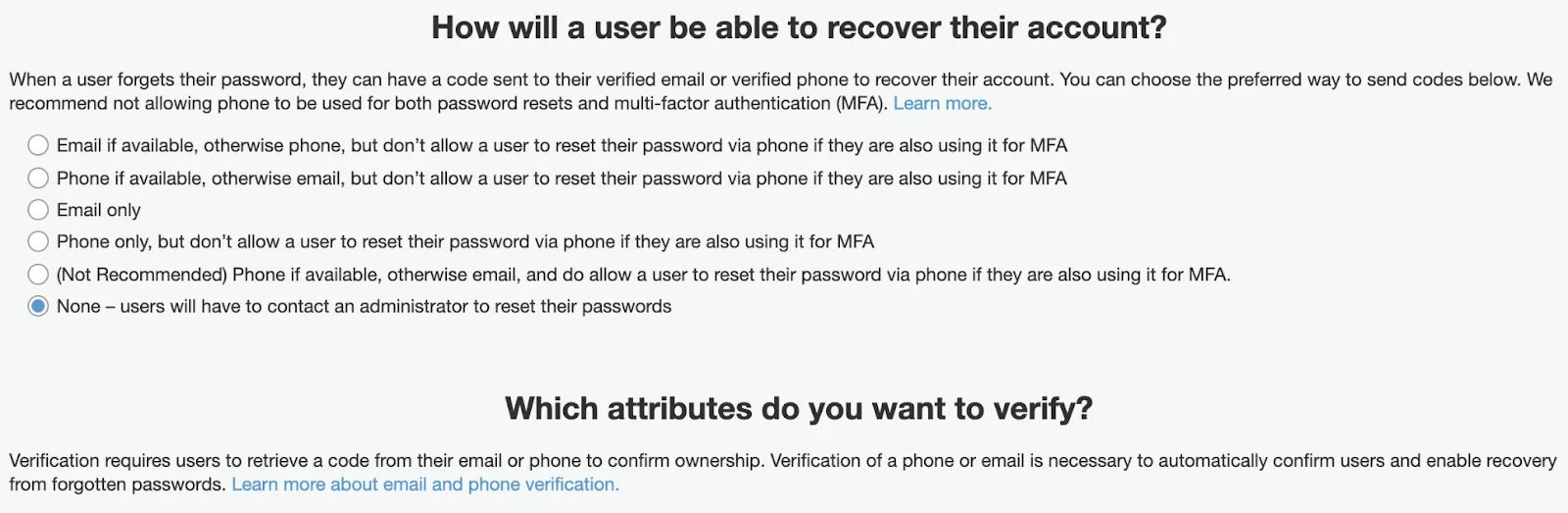
Next, you can define Password policy settings if you allow your users to be authenticated directly through Cognito using credentials.
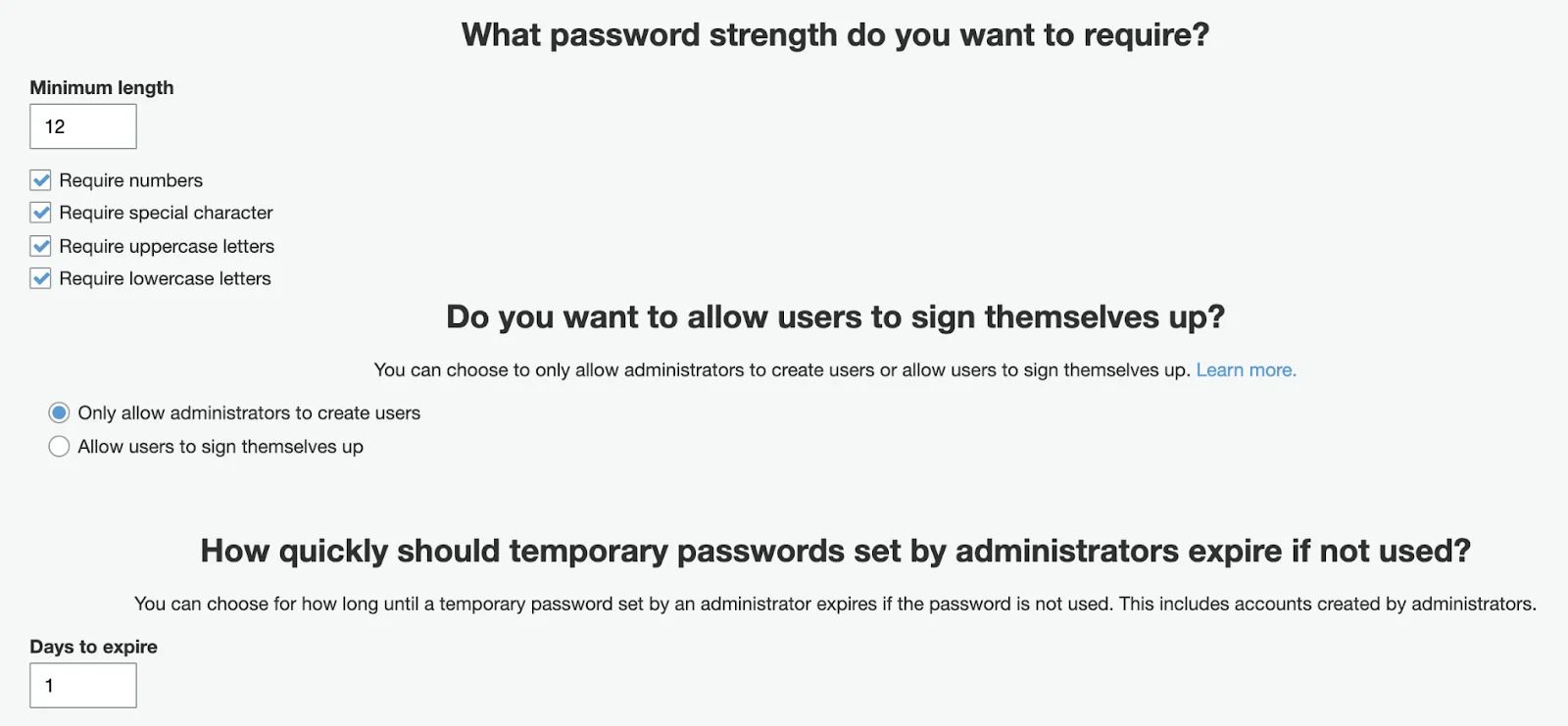
You may set as many as needed App clients for the same cognito instance. It can be a Dev setup with their own set of callback URLs and their own pairs of secrets.
On the screenshot below, you may see that users will be able to use 2 different SSO Identity providers, but not allowed to use User Pool (so, unable to enter credentials directly on Cognito).
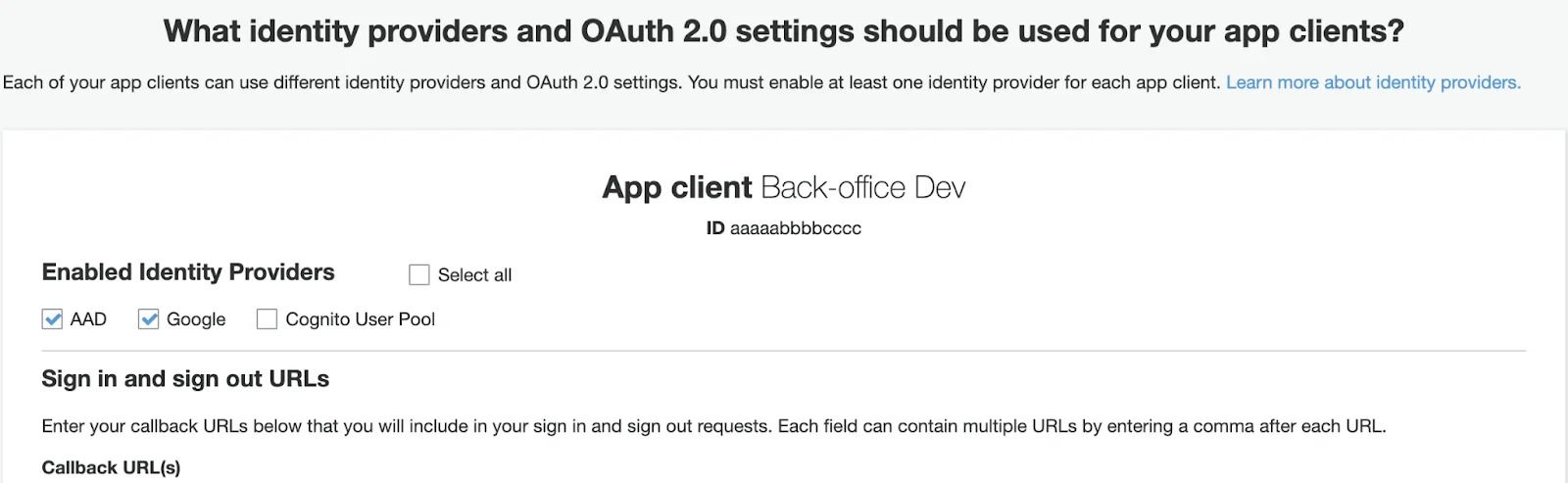
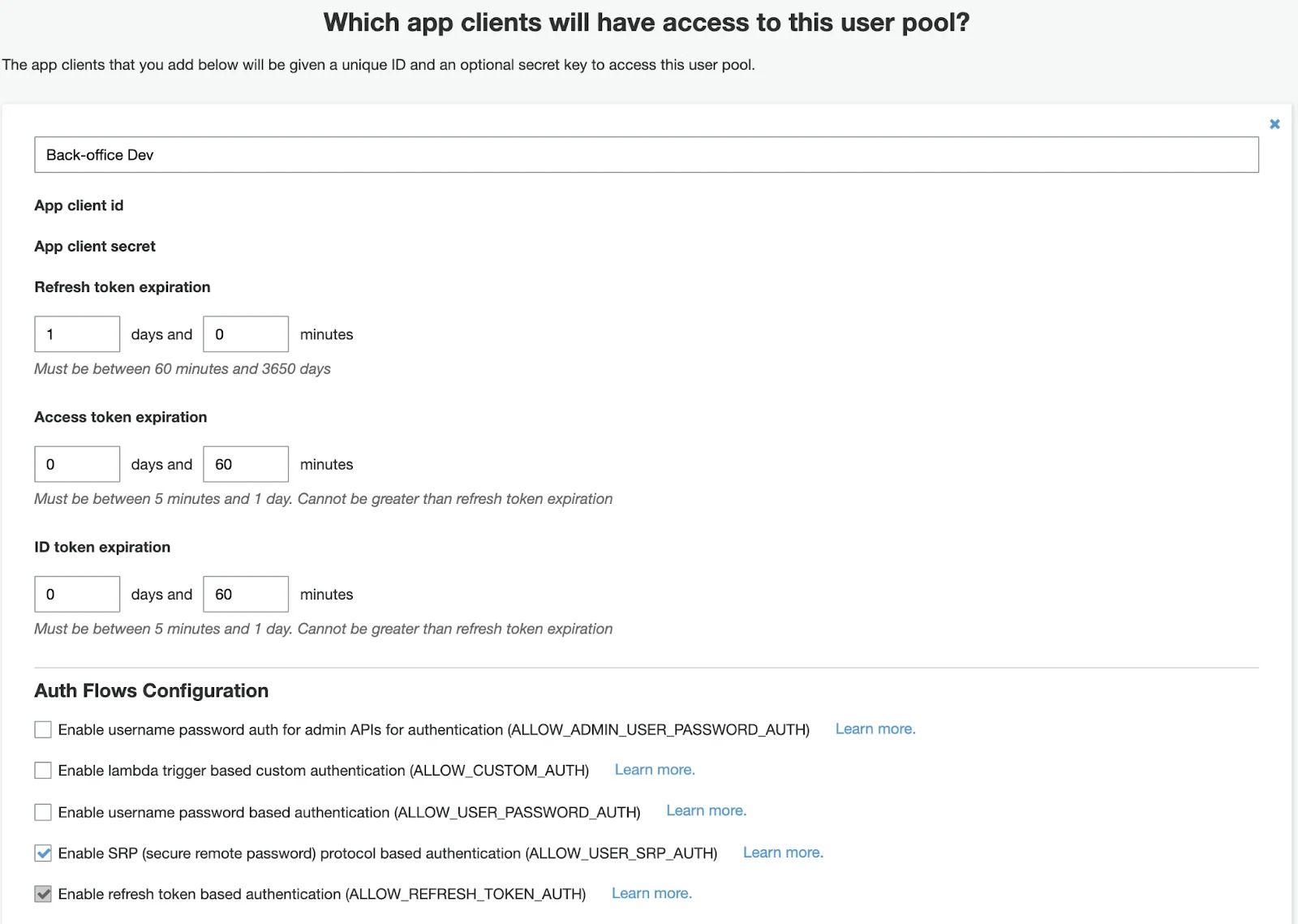
Then you can look up secrets, set tokens TTL and enable needed Auth Flows.
In our case, we need to enable SRP (secure remote password) protocol based authentication.
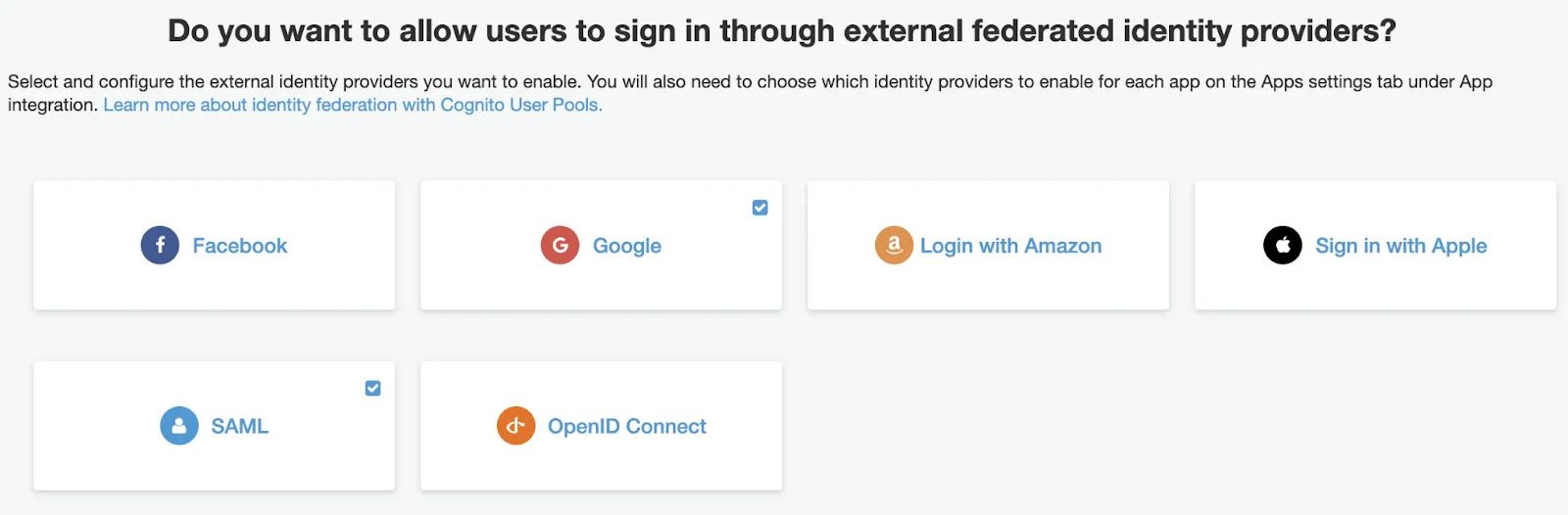
You can also add multiple SAML-based providers for different provider.
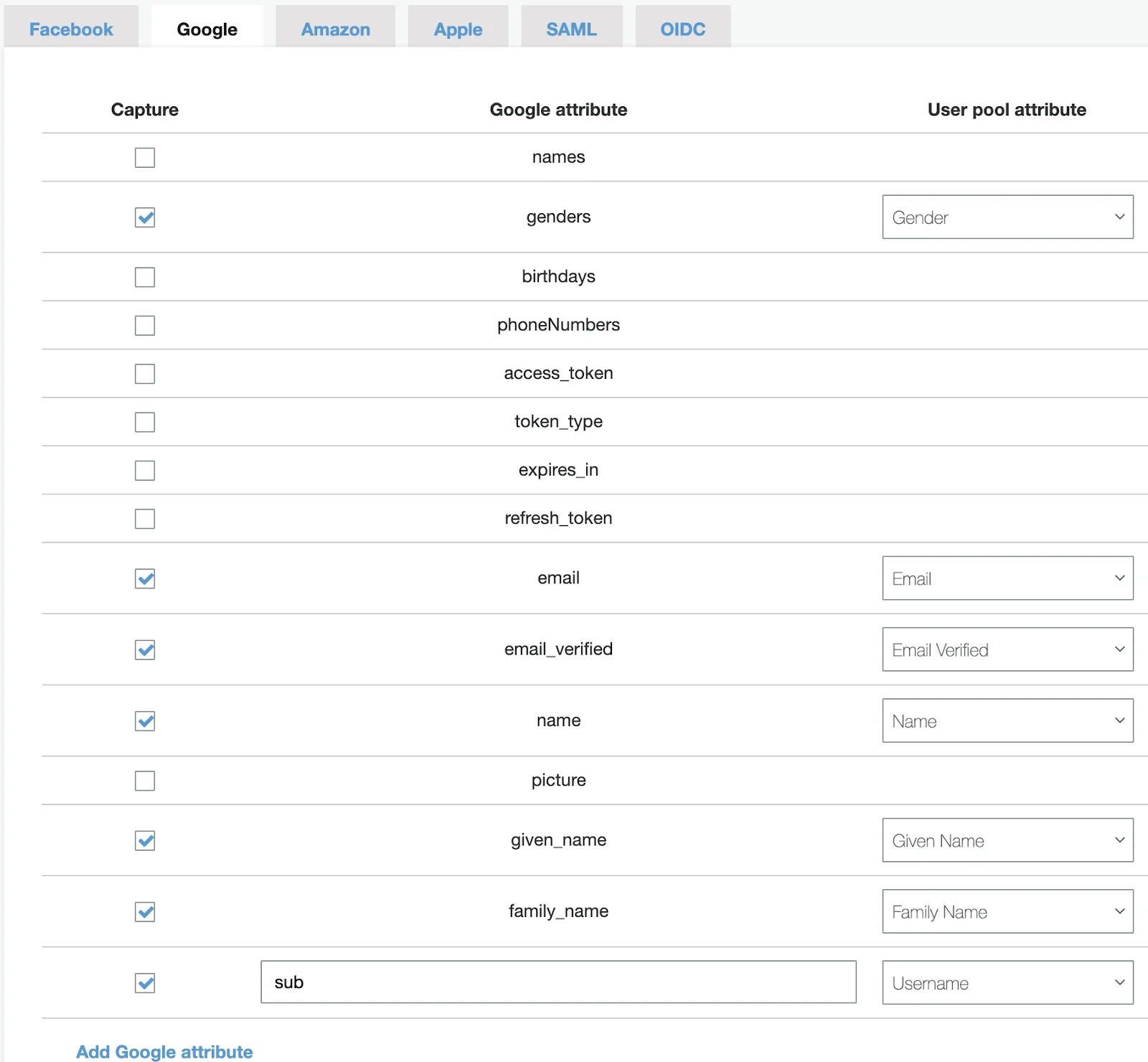
Example of Google sso:
That it's! Thanks for reading!

