Microservices architecture refer to the relatively small, independent development process that divides the system into services. Each service has its own logic, responsibility and can be deployed separately. Each of those services also needs to be authenticated and authorized.
Authentication and Authorization
Authentication and Authorization are two term when taking about securing applications that administrators use to protect application system and information.
Authentication is the process of identifying the user to provide access to the system. The user needs to supply login information to authenticate.
Authorization is the process of verifying the authenticated user to determines which permissions the user has. If user is authorized the process provide access to the specific information or allow user to execute a certain operation.
Microservices Authentication and Authorization Solution
Microservices provide loose coupling and separate context for each service. Each service will be broken down to focus on a specific business function or business requirement. So the application needs to authenticate and authorize each request to access the Microservices. There are two approaches:
- Access Token and API Gateway.
- Third-party application access.
Access Token and API Gateway
The API gateway is the single entry point for all clients. It provides a central interface for clients using these microservices.
In this approach, all requests go through the API gateway, a client sends a request to the API gateway responsible for routing it to the business service instead of having access to multiple services.
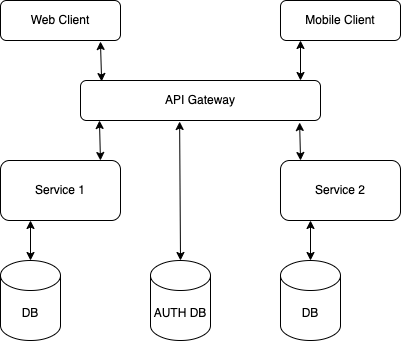
When client sends a request, the API gate way authenticate request and passes an access token that securely identifies the requestor in each request to the services. A service can include the access token in requests it makes to other services.
JSON Web Token (JWT) is a popular access token in Microservices Architecture.
The JWT is composed of three follow parts contains a list of claims which allow the receiver to validate the sender's identity.
- Header: contains the algorithm used for signing.
- Payload: the session data.
- Signature: calculated by encoding header and payload using Base64 encoded. The signature is used to verify the token has not changed or modified.
Third-party application access
In this approach, user using the third-party application to access to the microservices application. There are two ways:
- API token. The token is generateb by the user in the microservices application and provided for use by third-party application. Only third-party application are allowed to access the user's own data of the token. And when creating a token, user can set which data the token can access.
- OAuth. In this way the microservices act the role of the client in the Oauth architcture. When user access a microservice, it prompts the user to authorize a third-party application to use the corresponding access authority and generates a token for access according to the user's permissions.
In my application that using microservices architecture, I prefer to use JWT and OAuth together. The JWT is more lightweight and for access authentication between microservices it is sufficient, of course it can use to integrating with API gateway. But I think the Oauth is more suitable for integrating with API gateway, because it is generally used in third-party access scenarios.
References
- https://microservices.io/patterns/security/access-token.html
- https://microservices.io/patterns/apigateway.html
- https://oauth.net/2/