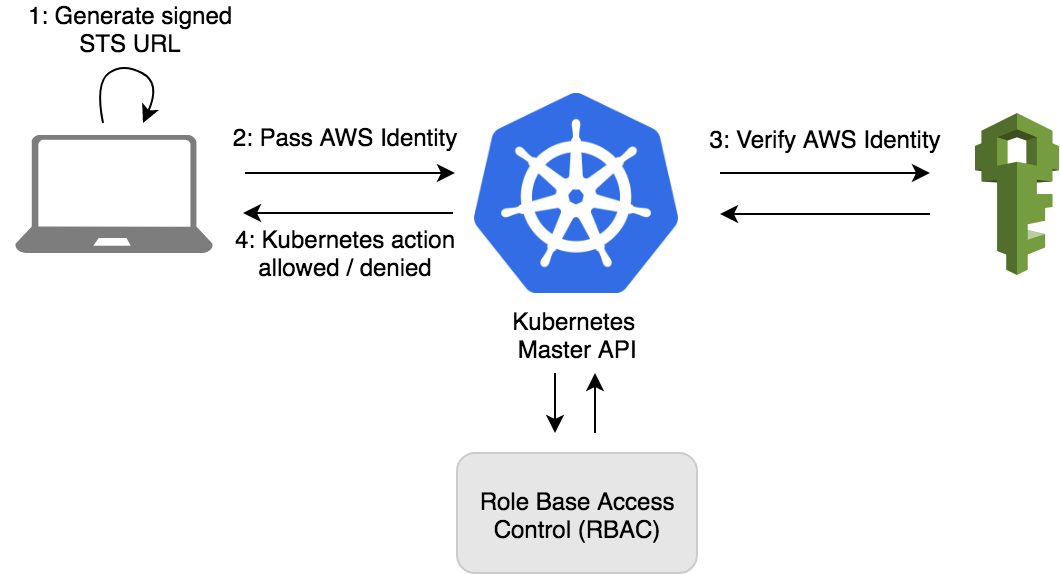
When you create an Amazon EKS cluster, the AWS Identity and Access Management (IAM) entity user or role, such as a federated user that creates the cluster, is automatically granted system:masters permissions in the cluster's role-based access control (RBAC) configuration in the Amazon EKS control plane. To grant additional AWS users or roles the ability to interact with your cluster, you must edit the aws-auth ConfigMap within Kubernetes and create a Kubernetes rolebinding or clusterrolebinding with the name of a group that you specify in the aws-authConfigMap.
In the scope of this post, i will create a EKS Cluster and a Bastion host. This bastion host is able to access to the EKS cluster and have a IAM Role associated with this.
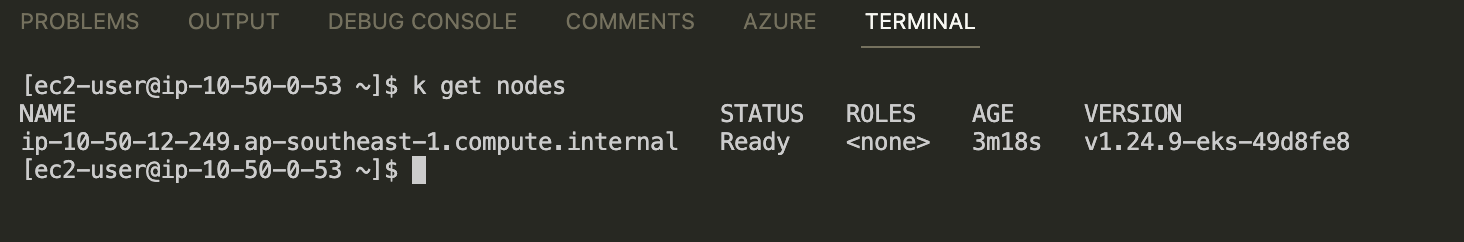
I already created a cluster with single node. First time when i tried to use aws clil to update cluster config and try to use kubectl to get cluster info, it will be denied due to the bastion host role didn't have access to any resource in cluster.
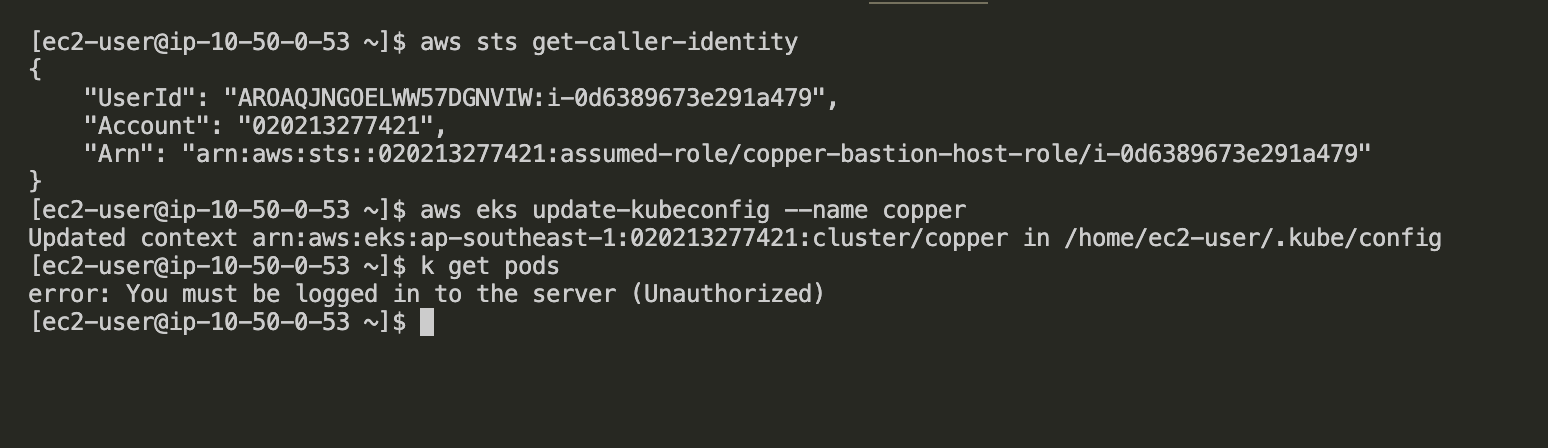
So what i need to do now is
- login with the access that created
cluster. - add
bastion roleto theaws-authconfig map. - verify the access of bastion host after adding permission.
Configure AWS Profile to login to EKS Cluster
First, login into bastion host, install aws cli v2 and also kubectl. To install aws cli v2 follow this link https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html. To install kubectl follow this link https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/.
After installing aws cli and kubectl , we need to configure new profile with AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY that came from the creator account.
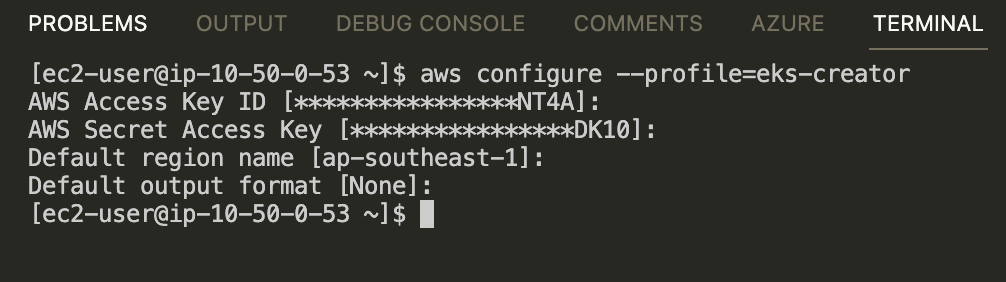
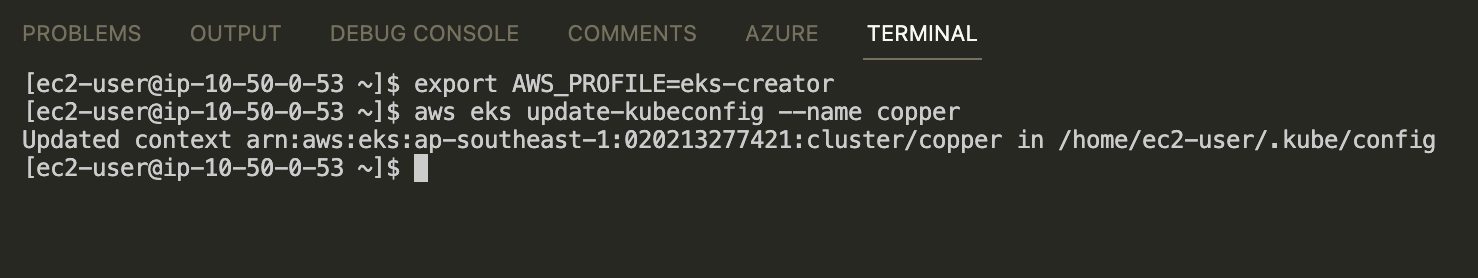
Login into Cluster
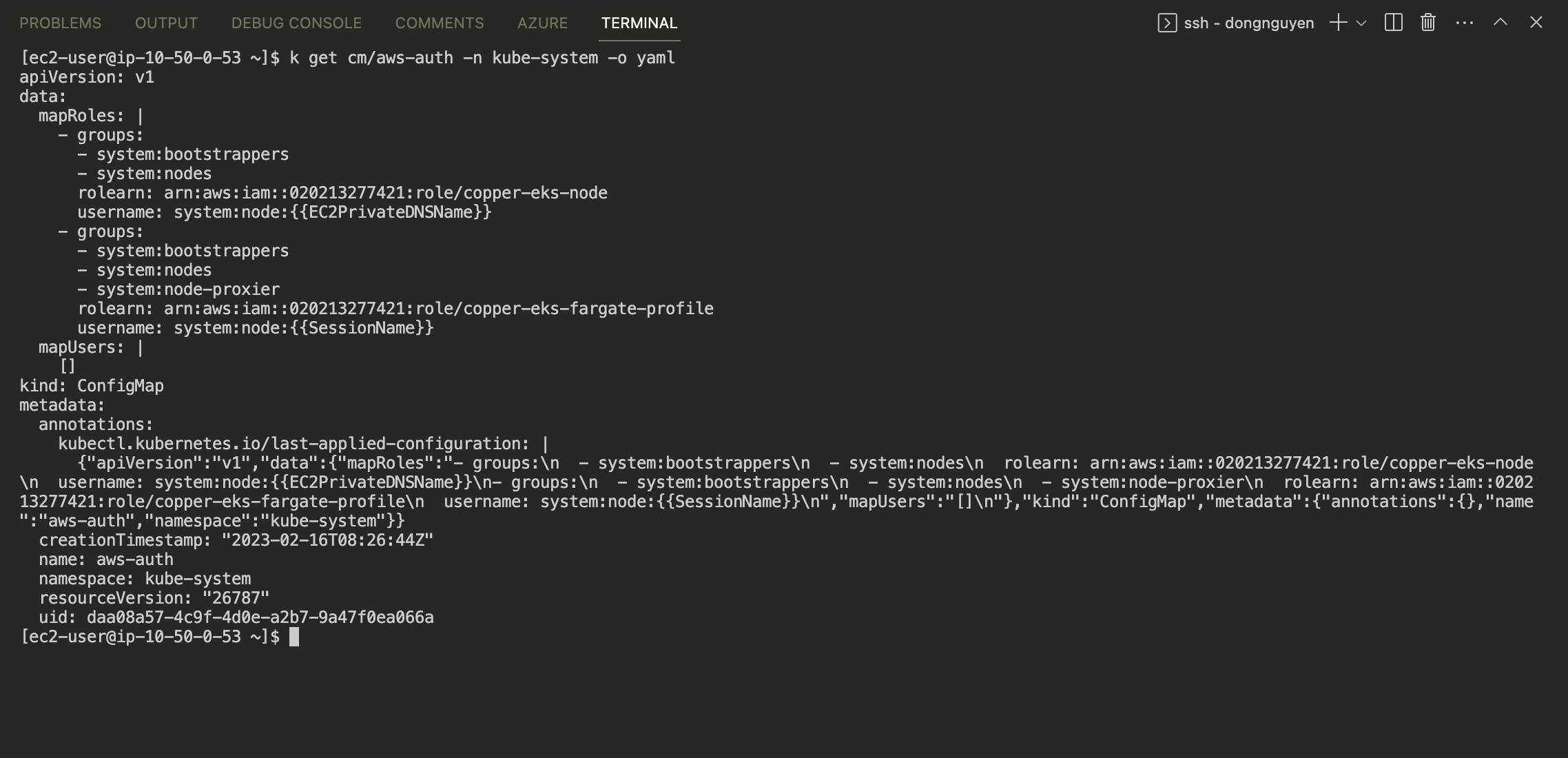
Try to get aws-auth configMap in kube-system namespace.
Add Bastion role to auth-auth configMap
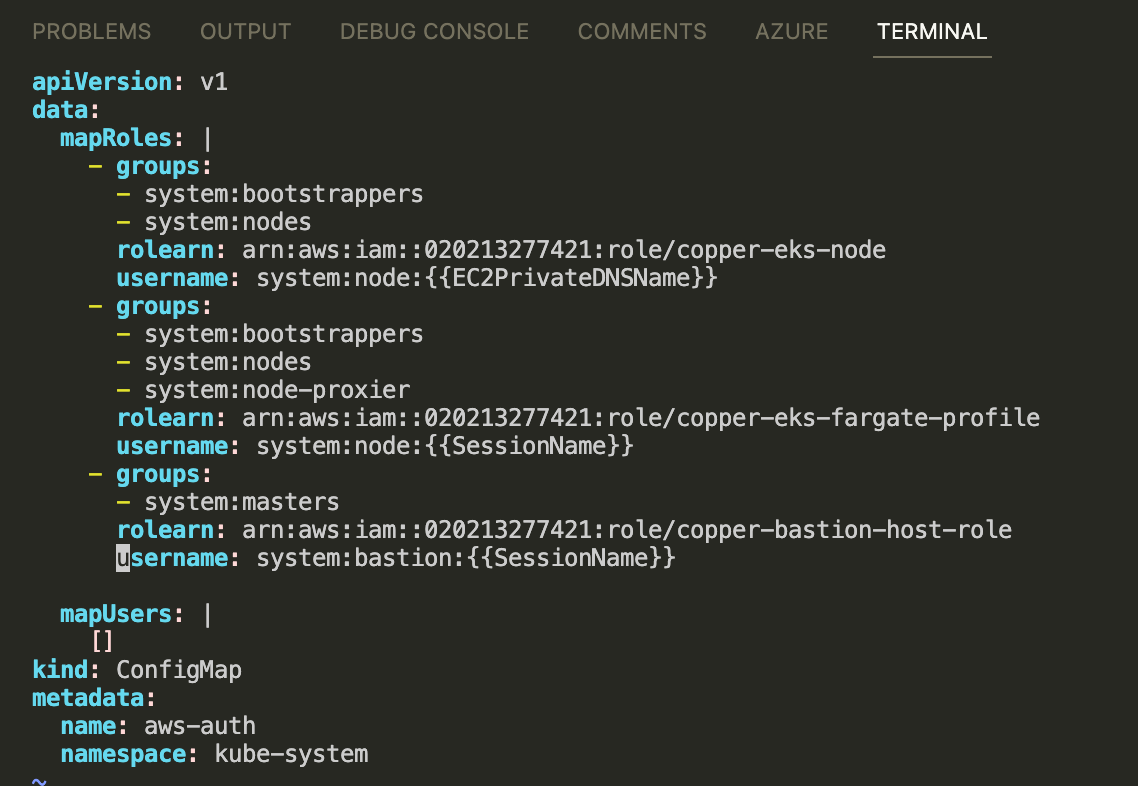
From the image above, you can see that i added item to mapRoles list.
- groups:
- system:masters
rolearn: arn:aws:iam::020213277421:role/copper-bastion-host-role
username: system:bastion:{{SessionName}}With this line, i give the administrator role to bastion host . And of cause you can change the group name and creating some role or cluster role binding to this group. But for demo purpose i will set it to system:masters group.
Next, we need to apply this change to cluster.
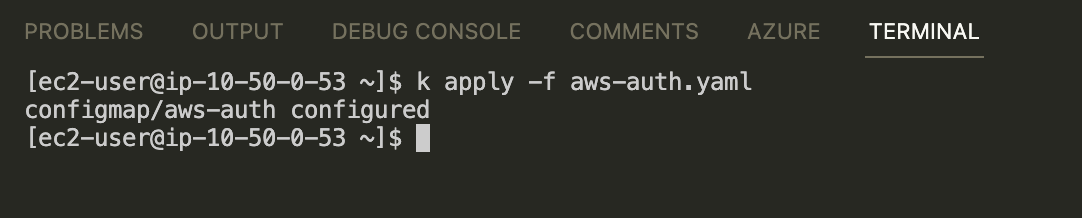
Test the permission with default profile
For now, let remove the eks-creator profile. Unset the AWS_PROFILE envionment.
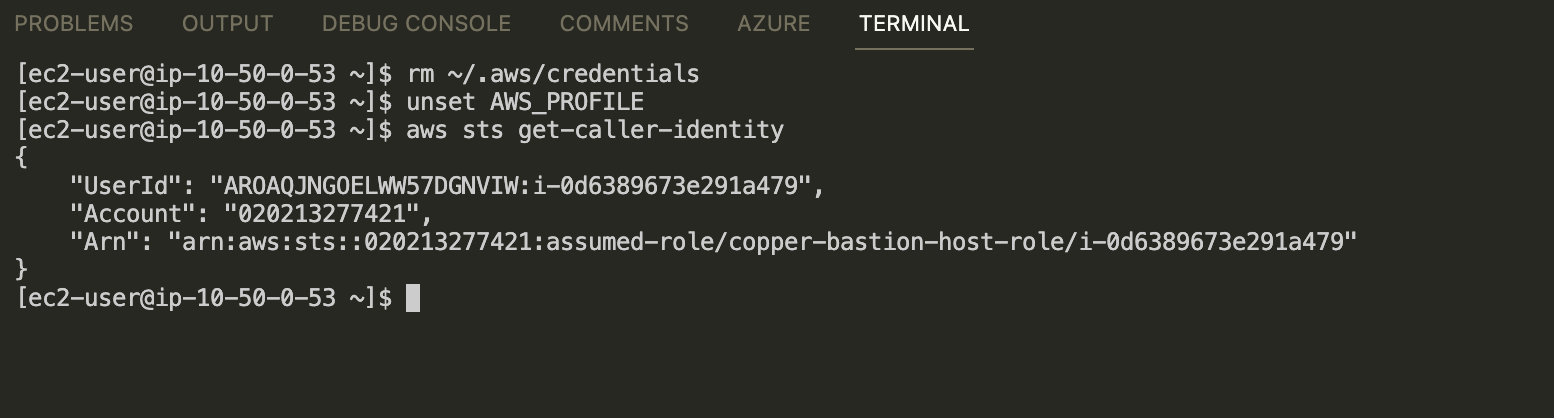
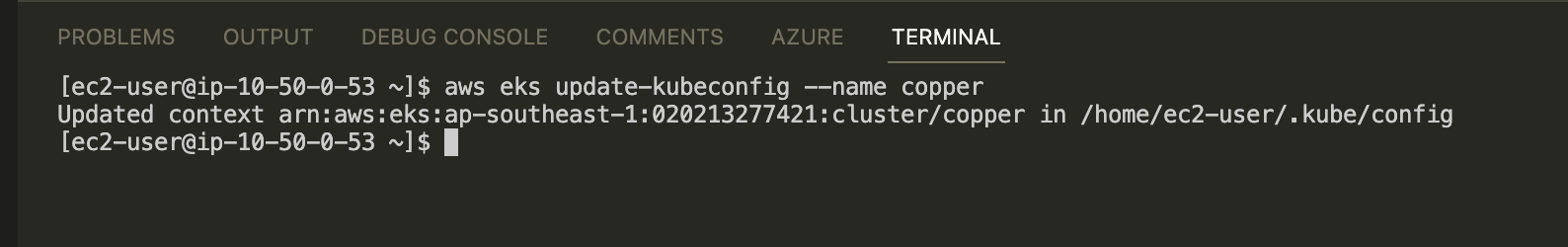
Update kubeconfig file. Before doing that, you need to make sure that bastion host has permission to describe cluster. The policy is same as below.
{
"Statement": [
{
"Action": [
"eks:DescribeCluster"
],
"Effect": "Allow",
"Resource": "arn:aws:eks:ap-southeast-1:020213277421:cluster/copper"
}
],
"Version": "2012-10-17"
}
Now, try to list all pods in the cluster.
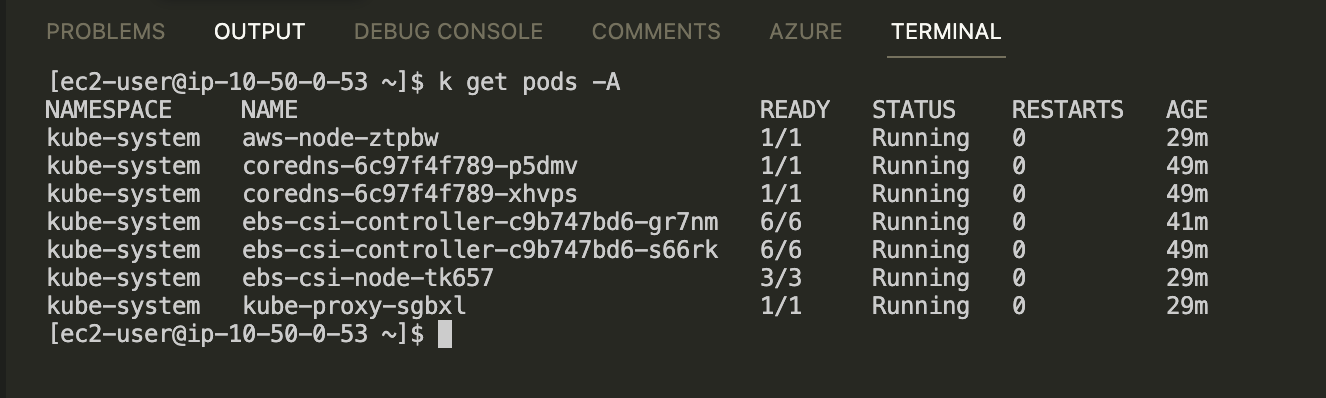
You can see that the bastion host has permission to do thing in the cluster so far.
That is, thank for reading.